We help you take control over your CVEs
We at Codiax help our customers identify, classify and mitigate CVEs using our
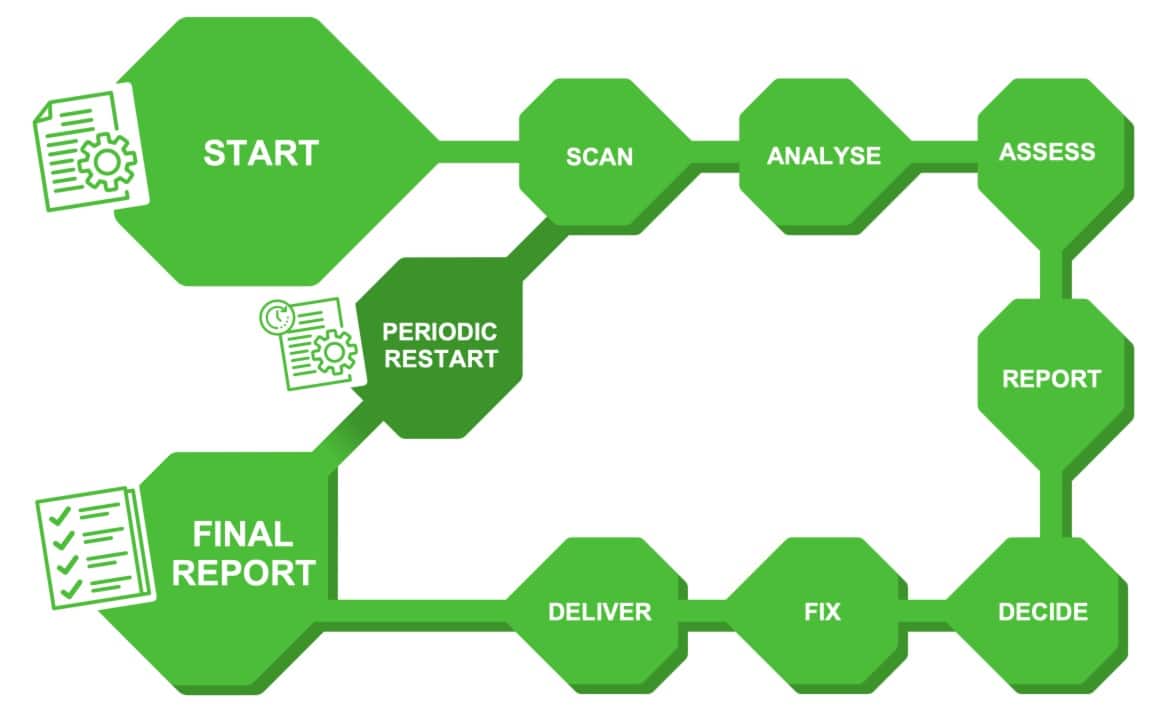
CVE Monitoring Process - CMP
With CMP we provide
- Frequent scanning of the CVE database for your system
- Assessment of relevancy of the applicable CVEs
- Mitigation with updates, patches or system redesign
- Reporting of final status after mitigation
All open source software contains vulnerabilities that can potentially be exploited, either intentionally or by accident. Results can be extremely serious depending on the impact of the vulnerability and the type of system the software is used in. Some examples of impacts are denial of service, performance degradation, system malfunction and ransomware. Systems that are connected to networks are usually more exposed to threats than systems that are not, but standalone systems may also be exposed. The open source software used in embedded systems needs to be reviewed for known threats and these must be mitigated appropriately.
Common Vulnerabilities and Exposures (CVEs) är ett definierat koncept för att identifiera, definiera och kategorisera offentligt identifierade cybersäkerhetssårbarheter. En CVE-databas finns tillgänglig på Internet och kan användas för att söka efter CVE:er som omfattar koden som används i ditt system.
CVE management
To successfully manage the CVEs that affect a system the following actions and considerations are normally needed
Questions that many companies face in relation to CVEs are how this scanning, assessment, mitigation and documentation shall be performed, and how frequently? What knowledge, experience and tools are required?
We at Codiax have many years of experience in this area. We offer our CVE Monitoring Services to our customers, in which we use the CVE Monitoring Process – CMP, to frequently go through all the above steps for our customers' systems.
CMP is a complete process from the first initial set-up to it completion with updated code and documentation. The process can be executed once, but we normally recommend it to be repeated on a regular basis.
At Codiax we have developed tools that assist in the different phases of the process.
The input to CMP can either be a CVE list from a Yocto build system scanning, or any list of open source packages used in the system. To understand how the system is designed and how the open source packages are used we need access to system documentation. If we also get access to the product build environment, that enables for more efficient assessment and update phases.
With our CVE monitoring services, Codiax can take responsibility for the complete CVE management for you.
